Learn Ethical Hacking: Ignite Your Potential for Positive Impact in 2023

In today’s technologically advanced world, cybersecurity has become a critical concern for individuals and organizations alike. As cyber threats continue to evolve and grow in sophistication, the demand for skilled professionals who can combat these risks has surged. Ethical hacking, a field dedicated to identifying and mitigating vulnerabilities in computer systems, has emerged as a pivotal component of cybersecurity efforts.
Beyond the exciting portrayals of hacking in movies, ethical hacking offers a rewarding career path, with professionals enjoying competitive salaries and the satisfaction of protecting digital infrastructures.
In this blog, we will delve into the realm of ethical hacking, exploring its increasing significance in the modern landscape and the potential it holds for aspiring cybersecurity enthusiasts.
You will also get to know what ethical hacking is, its types, how to learn ethical hacking, and careers as ethical hackers which can help you decide why to learn ethical hacking in 2023.
Without any further ado, let’s begin!
1. Ethical Hacking: A Brief Introduction –

Ethical hacking, also known as penetration testing or white hat hacking, involves legally and responsibly exploiting vulnerabilities to identify weaknesses in computer systems and networks.
Unlike their malicious counterparts, ethical hackers operate within strict legal and ethical boundaries. They work in collaboration with system owners, obtaining explicit permission and authorization to assess and probe the security measures in place. The objective is not to cause harm or compromise the integrity of the systems but rather to identify weaknesses and potential entry points that could be exploited by malicious actors.
The fundamental goal of ethical hacking is to proactively identify vulnerabilities before they can be exploited by adversaries. By actively seeking out weaknesses within the digital infrastructure of organizations, ethical hackers play a crucial role in fortifying their defenses. Through a systematic and comprehensive approach, they simulate real-world attack scenarios, analyze system vulnerabilities, and provide valuable insights and recommendations for strengthening security measures.
2. Types of Ethical Hacking
Ethical hacking encompasses various types, each focusing on specific areas of cybersecurity. Understanding these types will help you choose the areas you want to specialize in. Here are some common types of ethical hacking:
a) Web Application Hacking:
This type involves assessing the security of web applications, identifying vulnerabilities like SQL injections and cross-site scripting (XSS) attacks, and recommending fixes to enhance their security. By mastering web application hacking, you can help organizations secure their online platforms and protect sensitive user information.
b) Network Hacking:
Network hacking focuses on testing the security of computer networks, including routers, switches, and firewalls, to identify vulnerabilities and ensure a robust defense against unauthorized access. By becoming proficient in network hacking, you can assist organizations in building secure and resilient network infrastructures.
c) Wireless Hacking:
Wireless hacking involves securing wireless networks and preventing unauthorized access or attacks on Wi-Fi networks. With the proliferation of wireless networks, understanding wireless hacking techniques is essential for protecting organizations from wireless-based vulnerabilities.
d) Social Engineering:
Social engineering refers to exploiting human behavior and psychology to gain unauthorized access to systems. Ethical hackers use social engineering techniques to identify potential weaknesses in employee awareness and educate organizations about the importance of security awareness training. By mastering social engineering, you can assist organizations in fortifying the human element of cybersecurity.
e) Mobile Application Hacking:
As mobile applications continue to grow in popularity, securing them becomes crucial. Mobile application hacking focuses on assessing the security of mobile apps, identifying vulnerabilities, and recommending measures to enhance the protection of sensitive data stored within these apps. By mastering mobile application hacking, you can contribute to the secure development and deployment of mobile applications.
3. How to Learn Ethical Hacking:
Now that you have an understanding of ethical hacking and its various types, let’s delve into the step-by-step process of learning ethical hacking in 2023. It’s important to note that ethical hacking is a constantly evolving field, and continuous learning is essential to stay updated with the latest techniques and methodologies.
a) Start with Linux/Unix:

Linux and Unix-based operating systems are widely used in the field of cybersecurity. They offer robust security features, command-line interfaces, and a vast array of hacking tools. Familiarize yourself with Linux distributions such as Ubuntu or Kali Linux. Learn basic commands, file management, and shell scripting. Understanding Linux will provide a solid foundation for various hacking techniques and tools.
Linux, renowned for its open-source nature, stands as an operating system that offers unparalleled flexibility and extensive customization options. It is widely used in the cybersecurity community due to its stability and security features. By getting hands-on experience with Linux, you will develop a deeper understanding of the underlying system architecture and gain proficiency in using command-line tools, which are essential for ethical hacking.
b) Learn Programming Languages:

Proficiency in programming languages is essential for understanding the inner workings of software applications and identifying vulnerabilities. Start by learning programming languages such as C, Java, Python, PHP, and SQL.
- C: Learn C to understand low-level programming, memory management, and vulnerabilities like buffer overflows. This will enhance your understanding of how vulnerabilities can be exploited at a fundamental level.
- Java: Java is crucial for web application security. Gain proficiency in Java and understand its security libraries and frameworks. This will help you assess and secure Java-based web applications.
- Python: Python is versatile and widely used in cybersecurity. Learn Python for scripting, automation, and developing security tools. Python offers a rich set of libraries and frameworks that can assist you in various hacking tasks.
- PHP: PHP is used in web development, so understanding it will help you identify vulnerabilities like SQL injections. Gain knowledge of common PHP vulnerabilities and effective mitigation strategies.
- SQL: Understanding SQL is important for securing databases and preventing SQL injections. Learn about database security concepts, secure coding practices, and how to effectively protect sensitive data.
Programming languages provide you with the skills to analyze code, identify security flaws, and develop secure applications. Understanding the principles of secure coding will enable you to recognize common vulnerabilities and design resilient systems.
c) Get Good with Networking Concepts:
Networking is the backbone of computer systems, and a solid understanding of networking concepts is crucial for ethical hackers. Learn about TCP/IP, IP addressing, subnetting, network protocols (HTTP, DNS, FTP), and network topologies. Gain hands-on experience with tools like Wireshark for packet analysis and understanding network traffic.
Networking knowledge allows you to analyze network infrastructure, identify potential vulnerabilities, and assess network security configurations. Understanding how data flows across networks will enable you to identify weak points and secure them effectively.
d) Start Learning the Darkweb:
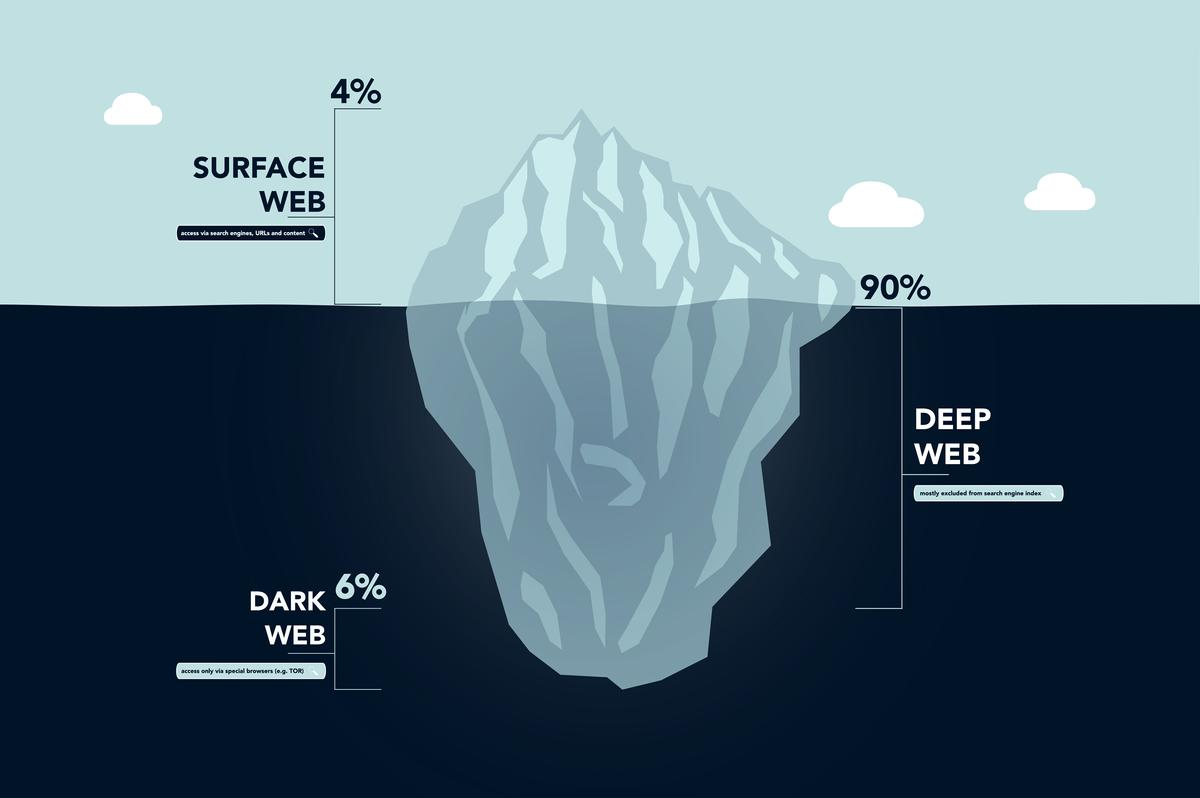
While ethical hackers do not engage in illegal activities, understanding the dark web can provide insights into the techniques used by malicious hackers. Familiarize yourself with the dark web’s concepts, hidden services, cryptocurrency transactions, and anonymous communication channels. It’s important to operate within legal boundaries and never engage in unlawful activities.
By exploring the dark web, you can gain an understanding of the illicit activities that take place there and the vulnerabilities that may be exploited. This knowledge will help you stay ahead of emerging threats and understand the motivations and tactics of malicious actors.
e) Learn Encryption and Decryption:
Encryption is vital for securing sensitive data. Learn about encryption algorithms, cryptographic protocols, and Public Key Infrastructure (PKI). Understand symmetric and asymmetric encryption, hashing algorithms, digital signatures, and certificates. This knowledge will enable you to evaluate the security of cryptographic implementations and recommend appropriate encryption measures.
Encryption is a fundamental aspect of cybersecurity. By understanding encryption and decryption techniques, you can assess the effectiveness of cryptographic solutions and identify potential vulnerabilities in their implementation.
f) Learn High-Level Concepts:
To become a well-rounded ethical hacker, it’s important to explore advanced concepts within cybersecurity. This includes penetration testing methodologies, vulnerability assessment techniques, incident response procedures, and digital forensics. Understand secure coding practices and principles to develop secure applications. Gain knowledge of secure network architecture and cloud security best practices.
High-level concepts provide you with a holistic view of cybersecurity. They allow you to approach ethical hacking from a strategic perspective and develop a comprehensive understanding of the different components that contribute to a secure environment.
g) Learn Ethical Hacking Tools:
Familiarize yourself with a wide range of ethical hacking tools. These tools will assist you in conducting various assessments, identifying vulnerabilities, and exploiting them responsibly. Some essential tools include:
- Wireshark: A powerful network analysis tool for capturing and analyzing network traffic.
- Nmap: A versatile port scanning tool for identifying open ports and potential vulnerabilities.
- Metasploit Framework: A powerful exploitation framework for testing and exploiting vulnerabilities in systems and applications.
- Burp Suite: A comprehensive web application security testing tool for identifying and fixing vulnerabilities in web applications.
- John the Ripper: A tool to check password’s strength and crack it.
It’s important to note that ethical hacking tools should be used responsibly and with proper authorization. Ensure that you understand the legal and ethical boundaries of using these tools.
h) Start Practicing:
Practice is crucial for mastering ethical hacking skills. Create a virtual lab environment by utilizing software such as VirtualBox or VMware. Create a network of virtual machines to simulate real-world scenarios. Practice techniques like network reconnaissance, vulnerability scanning, and exploitation. Always ensure that your activities are legal and conducted with proper authorization. It’s recommended to practice on your own systems or systems you have explicit permission to test.
Practical experience is essential for honing your ethical hacking skills. By creating a controlled environment, you can experiment with different tools and techniques, and understand the impact of your actions without compromising the security of real systems.
i) Join Communities:
Engage with the cybersecurity community to learn from experienced professionals, exchange ideas, and stay updated with the latest trends. Join online forums, participate in discussions, attend cybersecurity conferences, and participate in Capture The Flag (CTF) competitions to enhance your skills. Collaborating with like-minded individuals will not only broaden your knowledge but also expose you to different perspectives and real-world scenarios.
The cybersecurity community is a valuable resource for learning and networking. By actively participating in communities, you can access a wealth of knowledge, receive guidance from experts, and stay updated with the ever-evolving field of ethical hacking.
j) Get Certified or Join a Course (Optional):
Certifications can validate your skills and enhance your credibility as an ethical hacker. Consider obtaining certifications like Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), Certified Information Systems Security Professional (CISSP), or other relevant certifications. Additionally, you may choose to enroll in online courses or training programs that focus on ethical hacking and cybersecurity. These courses provide structured learning and guidance from industry professionals.
Certifications and courses can provide you with a structured learning path, access to resources, and recognition from the industry. While certifications are not mandatory, they can boost your career prospects and demonstrate your commitment to ethical hacking.
k) Make Projects:
Creating real-world projects is a great way to apply your knowledge and showcase your skills to potential employers or clients. Develop secure applications, build network infrastructures, or design secure architectures. Contribute to open-source projects, create security-related tools, or conduct independent research to deepen your understanding of ethical hacking. These projects will not only solidify your knowledge but also demonstrate your practical abilities and problem-solving skills.
By working on projects, you can demonstrate your skills and build a portfolio that showcases your capabilities. Real-world projects provide evidence of your proficiency and can significantly enhance your credibility as an ethical hacker.
4. Careers as an Ethical Hacker:
A career as an ethical hacker offers exciting opportunities in the field of cybersecurity. Organizations in various industries require skilled ethical hackers to protect their systems and data. You can work as an in-house security professional, join a cybersecurity consulting firm, or provide freelance services. With experience, you can specialize in specific domains such as web application security, network penetration testing, or incident response.
With that said here are some top careers as an Ethical hacker:
a) Penetration Tester:
Penetration testers, also known as ethical hackers, identify vulnerabilities in computer systems, networks, and applications. They simulate real-world attacks to test security measures and provide recommendations for improvement. This role requires technical skills and knowledge of hacking techniques.
b) Incident Responder:
Incident responders manage and mitigate security incidents. They detect and respond to breaches, investigate the root cause, and implement measures to prevent future incidents. This role requires analytical skills and the ability to work under pressure.
c) Security Consultant:
Security consultants provide advice on improving cybersecurity. They assess security measures, conduct risk assessments, and develop strategies to mitigate threats. This role requires technical expertise and communication skills.
d) Security Analyst:
Security analysts play a crucial role in monitoring and analyzing security events with the purpose of identifying potential threats. They use advanced tools to detect and investigate suspicious activities and respond to incidents. This role requires analytical skills and attention to detail.
e) Security Architect:
Security architects design and implement secure systems and networks. They create security frameworks, develop policies, and ensure the proper protection of IT infrastructure. This role requires an understanding of security principles and risk management.
Related : Top 7 Reasons Why you Should Learn Ethical Hacking
Ethical hacking is a rapidly growing field that requires responsible use of its power. As ethical hackers, it is crucial to recognize the impact of our actions and operate within ethical guidelines and legal boundaries. Upholding integrity, respecting privacy, and handling sensitive information responsibly are essential aspects of ethical hacking. Continuous learning and staying updated with the latest trends are vital, as the cybersecurity landscape is constantly evolving. Engaging with the cybersecurity community and nurturing a healthy work-life balance are also important for personal and professional growth.
In summary, ethical hacking offers exciting opportunities to protect digital systems and combat cyber threats. However, it is important to exercise caution, adhere to ethical standards, and continuously enhance our skills. By being responsible and committed to creating a safer digital world, ethical hackers can make a positive impact in the field of cybersecurity.
Frequently Asked Question
Learning Ethical Hacking in 6 months is possible, but the extent of your knowledge and skills will depend on various factors. These include your prior experience with computers and programming, the time and effort you dedicate to learning, the resources available to you, and the complexity of the topics you choose to explore. While 6 months may be sufficient to gain a foundational understanding of Ethical Hacking, mastering the subject and becoming proficient typically requires continuous learning and practical experience over an extended period.
Coders often prefer laptops that offer a balance of performance, portability, and compatibility with their preferred programming languages and tools. Popular laptop brands among coders include Apple (MacBook Pro and MacBook Air), Dell (XPS series), Lenovo (ThinkPad series), and HP (Envy and Spectre series). The choice ultimately depends on personal preferences, budget, and specific requirements such as processing power, RAM, storage capacity, and the operating system that best supports their coding environment.
Yes, you can learn Ethical Hacking on your own. With the abundance of online resources, tutorials, and communities dedicated to cybersecurity, self-learning has become a viable path for acquiring Ethical Hacking skills. It is essential to have a strong drive for self-motivation, discipline, and the ability to stay updated with the rapidly evolving field of cybersecurity. Practical hands-on experience, setting up a lab environment, participating in Capture The Flag (CTF) competitions, and collaborating with like-minded individuals can greatly enhance your learning journey.
There is no specific laptop brand or model exclusively used by hackers. The choice of the laptop depends on individual preferences, requirements, and the specific tasks involved in their hacking activities. Some hackers may prefer high-performance machines with advanced specifications, while others may prioritize portability and privacy features. Common considerations include processing power, memory, storage, compatibility with hacking tools and operating systems like Linux, and built-in security features. Ultimately, hackers select laptops that best align with their specific needs and allow them to carry out their tasks efficiently and effectively.
About the Author
Luqmaan Shaik serves as the Blog Specialist at Unikaksha, where he leads a team of technical writers dedicated to researching and providing valuable content for blog readers. With a wealth of experience in SEO tools and technologies, his writing interests encompass a wide range of subjects, reflecting the diverse nature of the articles. During his leisure time, he indulges in an equal balance of web content and book consumption.
 Related Posts
Related Posts
|
Offerings
|
FutureFirst
|
SmartStart
|
GradEdge
|
SelfMastery
|
|---|---|---|---|---|
|
Doubt clearing session
|
                                          |
                                          |
                                          |
                                          |
|
No of job opportunities
|
15 | 25 | 15 | 3 |
|
Course Access
|
5 Years | Lifetime | Lifetime | 5 Years |
|
Free Library Courses
|
                                          |
                                          |
                                          |
                                          |
|
Job Assurance
|
                                          |
                                          |
                                          |
                                          |
|
Language
|
English/Hindi | 5 Language options | English/Hindi | English/Hindi |
|
Live classes
|
100% | 100% | 100% |                     |
|
Offline
|
                                          |
                                          |
                                          |
                    |
|
Industry Expert Sessions
|
                    |
                                          |
                    |
                    |
|
Internship (IOP)
|
                                          |
Guaranteed | Guaranteed | Based on evaluation |
|
1:1 Mentoring sessions
|
                    |
                                          |
                    |
                    |
|
Customer Support
|
                                          |
                                          |
                                          |
                                          |
|
Dedicated Program Manager
|
                    |
                                          |
                    |
                    |
|
Opt for Placement services
|
Compulsary |                                           |
                                          |
                                          |
|
Career Support
|
1 Year | 18 Months | 1 Year | 3 Months |
|
Regular assessments
|
                                          |
                                          |
                                          |
                                          |
|
Report cards
|
                                          |
                                          |
                                          |
                    |
|
Career Guidance
|
                                          |
                                          |
                                          |
                    |
|
Certificates
|
                                          |
                                          |
                                          |
                    |
|
Scholarship
|
                                          |
Available | Available |                     |
|
Trial Class
|
1 week | 1 week | 1 week |                     |
|
Outside placement
|
Paid | Allowed | Allowed | Allowed |
|
Premium Jobs
|
                    |
                                          |
                    |
                    |
